DICEGRID
The world's first power electronics CTF challenge. Includes custom-built power meters and protection circuits.

Mecanum MPC
mpc implementation for mecanum-wheeled robots. dynamics model derived using lagrangian mechanics. system parameters identified using optuna and raytune.
cpu-fuzzer
x86_64 semantics fuzzer with knowledge of the entire instruction set (all 1500+ ops). has discovered a confirmed register allocation bug in AMD Zen 4 cpus.
mopos
simple operating system (and homemade x86 bootloader) supporting multitasking and preemption
CVE-2022-0185
critical privilege escalation in the linux kernel and exploit for it. awarded $33k by google.
chopcoin
litecoin fork from before it was cool. the only thing that makes it unique is that it's mine.
wireguard-java
Java implementation of the wireguard vpn protocol. written 100% in java, with no dependencies, by using the ffi api (project panama) to directly invoke tun syscalls.
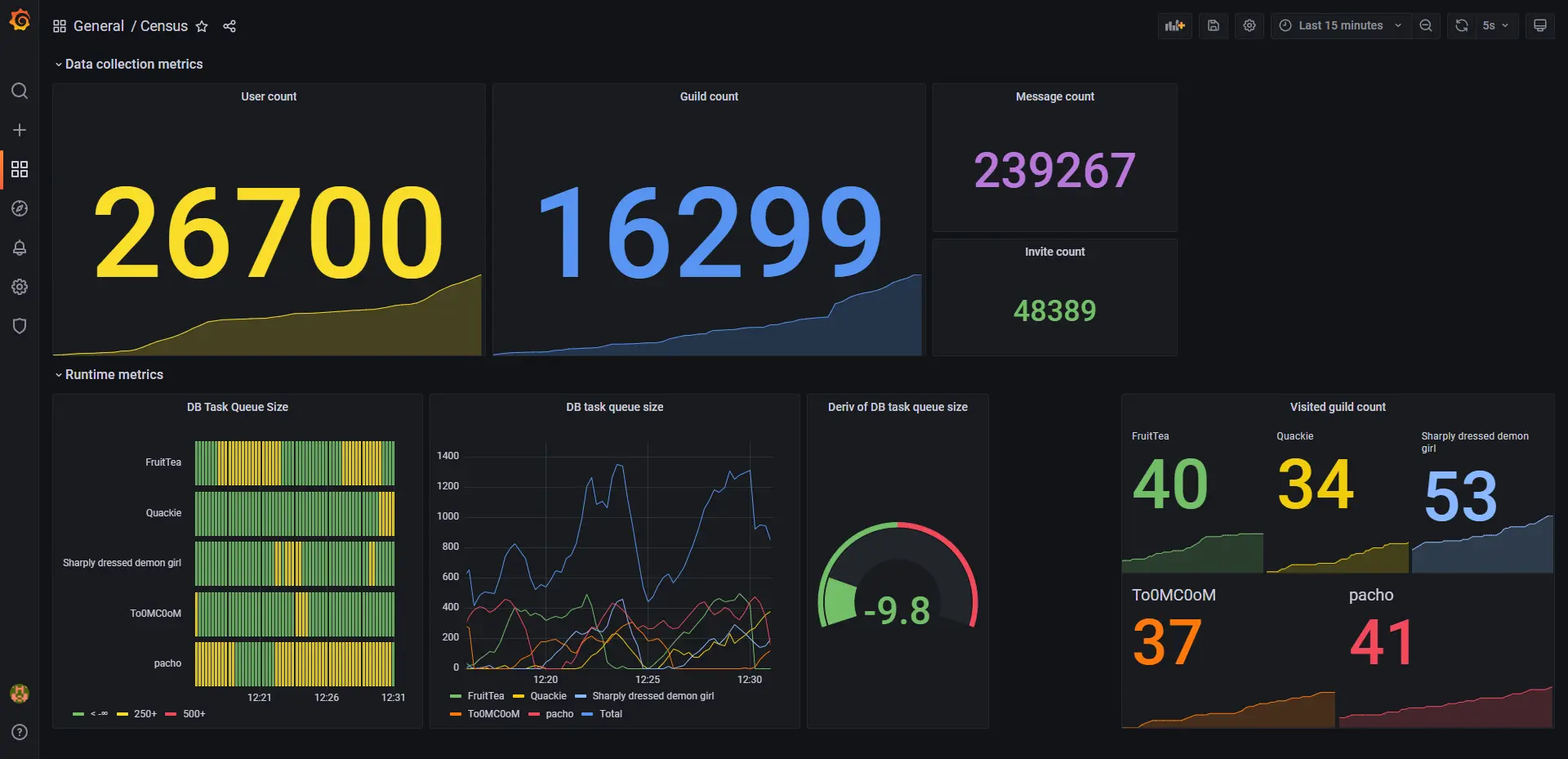
Discord Census
a Discord crawler that uses puppet Discord accounts to spider servers and log members, messages and invites as it goes
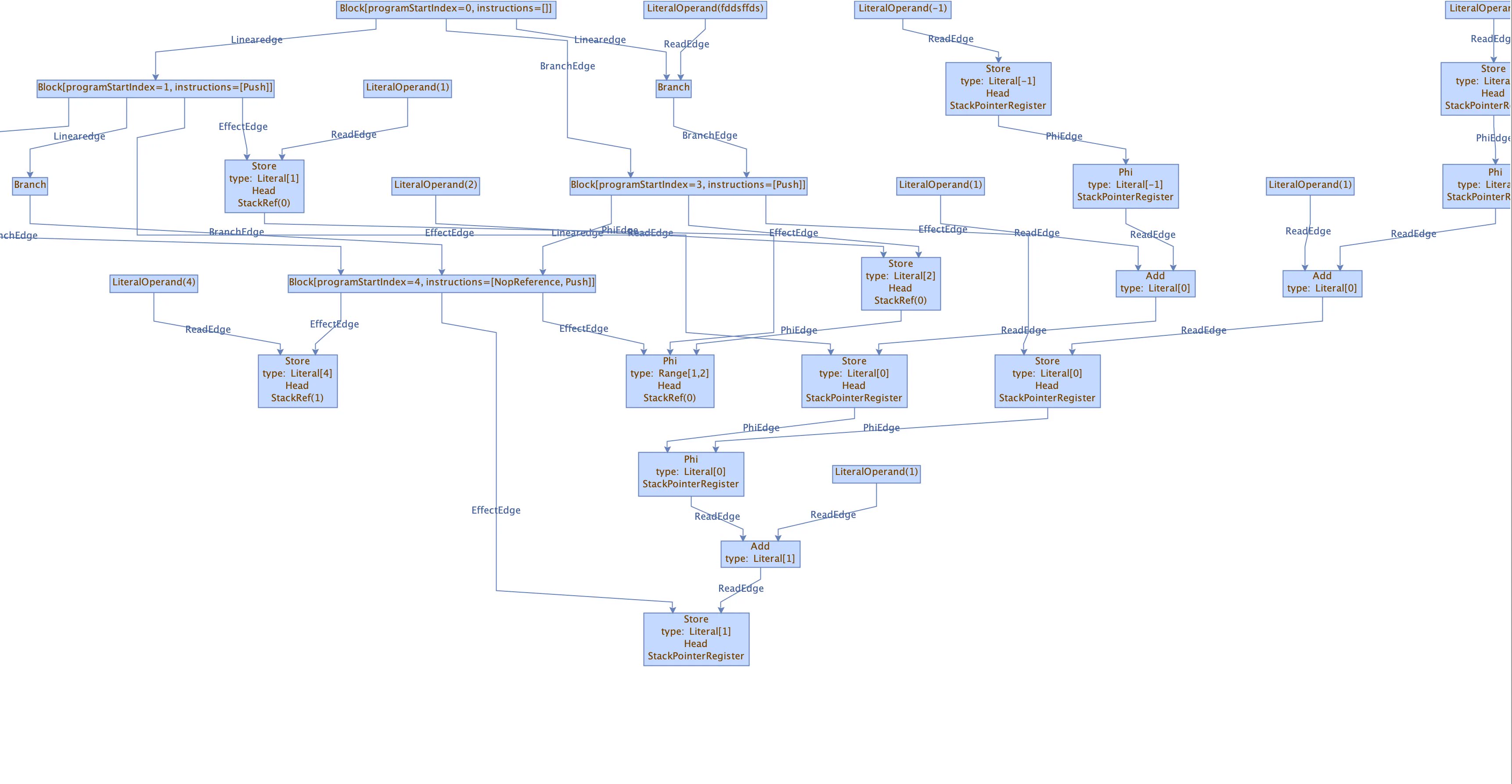
graal-bindgen
generates safe bindings between Rust and Graal Polyglot so that you can use Java types and methods as if they were ordinary Rust methods
graal_bindgen_macros::class! [java.util.ArrayList<E> {
new();
E get(int index);
boolean add(E e);
E[] toArray();
}];
let list = ArrayList::new();
let list_in_list = ArrayList::new();
for i in 0..100 {
list_in_list.add(i);
}
list.add(list_in_list);
let array_from_list = list.get(0).toArray();
for i in 0..100 {
println!("{}", array_from_list.get(i).unwrap());
}Decompiler
stack-tracking decompiler that uses a soup-of-nodes representation to lift machine code
CTF challenge: Midenios
array OOB introduced in spidermonkey (firefox JS engine) patch. bug exploited using shellcode heap spray + egg hunting.
Description |
The Government have obtained intelligence suggesting that Midenios have been selling zero-days to North Korea, and suspect the organisation's ringleaders live in NATO-cooperative countries. Unfortunately, Midenios use Tor Browser to communicate with potential customers, so an IP logger would be ineffective. Whilst not as notorious as V8, Tor Browser's JS engine is actually less hardened than its competitor, and bugs as simple as relative ArrayBuffer OOBs can be catastrophic. Can you find a way to gain RCE and identify bad actors? |
Difficulty |
hard |
Flag |
HTB{c0ry_d0ctorow_was_wr0ng}
|
Release |
midenios-dist.tar.gz |